Understanding how bad guys reuse infrastructure will show you the areas of your network to target when investigating new threats and reiteration of old malware.
Security staff put a lot of emphasis on advanced persistent threats, or APTs, and rightly so. They are extremely difficult to defend against if a hacker is specifically targeting an organization. But with everyone's focus on APTs, we may be missing a different type of attack vector: advanced persistent infrastructure.
We tend to view threats in a silo, often ignoring correlating histories. By doing that, we miss vital information about attacks. In this case, intruders are using patterns that weren't readily picked up in the past. They aren't looking to buy a new server for every new attack. Instead, threat actors will reuse IPs and domain names across multiple campaigns.
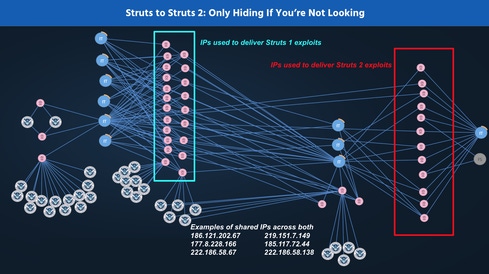
The evolution of the Apache Struts vulnerability is a good example of how threat actors use advanced persistent infrastructure as an attack vector. In 2014, there were initial reports of exploits against the Struts vulnerability. In early 2017, new exploits were discovered in a Struts 2 vulnerability. We noticed the two exploits followed a very distinct pattern.
According to data submitted by qualified companies without attribution on TruSTAR's threat intelligence platform, we can now see threats trending across major industry sectors like retail, financial services, cloud, and healthcare. For the past four weeks, indicators of compromise (IOCs) associated with Apache Struts 2 have been trending across our all of the users who submit data to our platform. Looking back at historical report data in the Struts 1 and Struts 2 vulnerabilities, we found that the IP addresses used with the original Struts are now being used with the new Struts.
This lead to some interesting observations:
Tactics May Change But IPs Don't. Unless they are a member of a big crime organization, most bad guys don't have the money to buy new IP addresses and domains over and over again. Hence, when an IP address comes online we should know exactly what it is tied to and its history.
Hackers Feed on the Lazy. The connections between Struts 1 and Struts 2 created a new reality: as is often the case, when a new zero-day exploit is reported, organizations are slow to move on patching these things. The bad guys know they have to act quickly to make use of the exploit. What they do is simply retool their favorite form of malware, and then use the infrastructure access they have in place, like IPs and domains, to launch the new attacks.
Recognizing how these IP addresses and domains are reused allow you to predict what may be coming down the pike. Look at your activity history. That will give you an idea about what to be on the lookout for. When you see a new version or variant of a known malware, monitor old IPs and domains that directly correlate for new activity.
By understanding how bad guys reuse infrastructure, you’ll have a better idea of the areas of your network to target when investigating a new threat, especially when it is a reiteration of an old malware.
Related Content:

Join Dark Reading LIVE for two days of practical cyber defense discussions. Learn from the industry’s most knowledgeable IT security experts. Check out the INsecurity agenda here.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




