Security spending and staffing are rising, but restrained resources are tempering market growth.
The IT security market is often painted as a non-stop growth curve with no end in sight. But many analysts who have studied market trends say despite recent increases in spending and hiring, the market paradoxically is being slowed by a shortage of resources.
In some cases, upper management is putting a cap on spending and hiring. In the recently published 2017 Black Hat Attendee Survey, most security professionals say they are increasing hiring and spending. Yet, some 71% of security professionals do not feel they have enough people to handle the threats they will face in the coming year. Fifty-eight percent say they don’t have enough budget.
"Security spending is based on failure, rather than need. The more secure that you feel, the less you spend," says John Pescatore, director of emerging security trends for SANS Institute.
Cybersecurity indeed is growing, but just not as fast as you'd think.
IT security spending growth also is hampered by a lack of available talent to pull off the needed projects, says Jeff Pollard, principal analyst with Forrester Research.
"There are capacity restrictions," says Pollard. "It is not the available funds in the budget, but the fact that you can only do three, four, or five big projects a year because of the number of people, service providers, and employee skill sets you have."
One report by CyberSecurity Ventures pegs IT security spending to soar beyond $1 trillion in revenue over the course of a five-year period ending in 2021, with 12% to 15% annual growth.
But a larger pool of industry analysts and players are expecting a slightly less robust future - with annual revenue growth of less than 10%. Cisco Systems and IBM, for example, reported security revenue growth of 9% in the third quarter and 9% in the first quarter, respectively.
Gartner is projecting a more muted level of worldwide IT security spending. The research firm is predicting annual revenue growth to increase along the lines of 7.6% in 2017 to 8% by 2020, says Lawrence Pingree, a Gartner analyst and vice president.
Pingree says IT security spending is expected to reach $90.1 billion this year and increase to $113.1 billion by 2020.
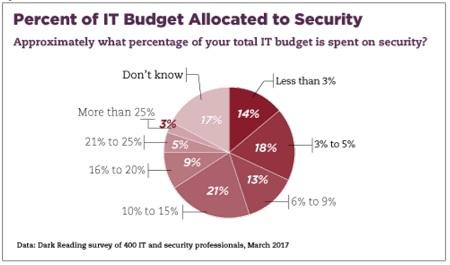
And when viewing security spending as a percentage of the overall IT budget, nearly half of 400 IT professionals surveyed in a Dark Reading report, "How Enterprises Spend Their Security Dollars," say they expect to allocate 9% or less on security, with a sizable portion of this spend coming in at 5% or less. This level of security spending will largely remain in place for the next 12 months, given 40% of survey respondents noted they did not expect an increase in their overall IT budget, which in turn trickles down to the security budgets.
One possible contributor to tight security budgets and tempered growth in the industry is a desire by companies to achieve greater efficiencies with their existing technology. "Rather than spending more on security, boards are asking 'what are you doing to spend less and do it in a better way than what we are doing?'" Pescatore says. "Security in depth is spending in depth."
IT Job Growth
The shortage of workers may also be putting a cap on security market growth. When 2022 rolls around, IT security trade organization ISC2 is predicting a 1.8 million shortfall of cybersecurity professionals to fill empty or expansion positions around the world. That, in turn, might explain the bullish job growth forecasts from the Bureau of Labor Statistics that says information security analysts should see an 18% rise in job growth between 2014 to 2024.
However, recruiting firm Robert Half Technology expects a more muted growth rate of 5% for IT security positions. Robert Half and other IT security recruiters note that with a limited pool of infosec professionals to hire, that alone is keeping a lid on massive hiring growth.
A recent Dark Reading report on Surviving the IT Security Skills Shortage found that only 14% of the 400 IT and IT security professionals surveyed believe there are a sufficient number of skilled IT security professionals available on the market.
Meanwhile, the UK's separation from the European Union under Brexit also contributed to a slowdown in IT security hiring, as a number of new programs were put on hold that would otherwise drive jobs growth, says Owanate Bestman, an information security contract consultant for recruiting firm Barclay Simpson. The GDPR, however, is an IT security jobs driver, he says, with an estimated 30% of posted positions in the first quarter having some relationship to the new regulations.
There may not be enough infosec professionals to go around to fill those GDPR slots as well as other vacant security positions, so companies will need to seek out other ways to fill the void. Ray Rothrock, CEO of RedSeal, predicts that this will not necessarily equate to IT security growth.
"How do we prepare for this chronic skilled labor shortage?" Rothrock asks. "We need to learn to work smarter, to do more with less, to prioritize assets and vulnerabilities, to automate and integrate as much as possible."
Related Content:
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




