When deploying ransomware is as easy as ordering a pizza, the best defense is through better threat intelligence sharing.
With "Philadelphia," a slick ransomware-as-a-service interface that enables almost anyone to launch a sophisticated ransomware campaign, suddenly, deploying ransomware is easy as ordering a pizza. The criminal developers behind Philadelphia even had the heart to offer a “mercy” feature should a victim plead for access to ransomed family photos of lost family and friends.
Welcome to the new world of commodity malware!
As the co-founder of a threat intelligence exchange platform, I see of lot of trending campaigns before they reach mainstream, and Philadelphia typifies many of the new age indicators we’re starting to see in incident data from companies across the cloud, finance, and healthcare sectors.
Below are some key insights about this new era of commodity malware so that you can spot patterns within your own data.
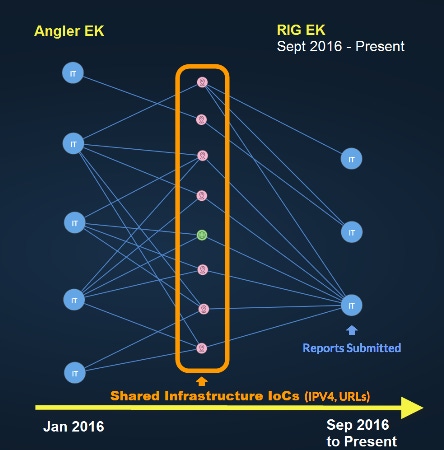
Insight #1 - The Exploit Kit Playbook: Many incident reports show multiple ransomware campaigns relying on an easy-to-buy RIG exploit kit, and then combining it with commoditized ransomware like Cerber and Locky. The playbook for creating new ransomware campaigns has been written and everyone is following it.
Insight #2 - Block and Tackle: Blocking a specific exploit kit or ransomware software will lead to short-term disruption of some campaigns but bad actors will find a different exploit kit or ransomware to weaponize and evolve into a new campaign.
For example, from January to June of 2016, Angler was the predominant exploit kit being seen in reports submitted to the wider security community until it was disrupted due to arrests of a criminal hacking gang in Russia. When the Angler exploit kit went down, cybercriminals began searching for a new go-to exploit kit, and in early September 2016 the RIG exploit kit became the predominant cybercriminals exploit kit.
Insight #3 - Low-Effort, High-Efficacy: Malware usually requires additional steps to monetize a successful exploit. Whether it is pulling exfiltrated data from the first level C2 or stolen passwords, the bad guys have to do the work of posting that information for sale after packaging the data in a specific size and/or format. On the other hand, ransomware is fire and forget. As soon as it hits a system the payoff is instantaneous.
In previous malware models there was usually a way for the user to remove or mitigate the issue. If the user gets a keylogger, RAT, or rootkit on their system there is almost always a way to remove the offending malware. Sometimes the steps to remove the malware can be tedious, or special tools are needed, but there is a path to a solution. This is not the case with ransomware. Pretty much all ransomware utilizes asynchronous encryption, making reversal extremely difficult.
It’s Not Just You
Ransomware campaigns bar access to critical data but they can also be used to disrupt system operations. Recall the Hollywood Presbyterian ransomware attack just over a year ago. The attack disrupted emergency room operations and patients had to be diverted to other hospitals.
The trend of commoditized ransomware raises an even larger issue within the security community: companies need to stop assuming they are being singled out for attacks. The truth is, you’re not that special. In fact, according to our latest platform analysis, 65% of our threat reports are correlating across companies regardless of sector.
There is absolutely no reason that after one victim has been hit by a particular ransomware attack others must fall victim to the same attack. What we’re seeing in the media and from our own platform data insights underscore the fact that commoditized ransomware campaigns will become increasingly opportunistic, and will not be as targeted.
As hacks continue to be replicated with more ease, the private sector must not fight alone. Exchanging threat intelligence to identify trending campaigns and provide context to mitigate against these campaigns is the only path forward.

Related Content:
About the Author(s)
You May Also Like
Defending Against Today's Threat Landscape with MDR
April 18, 2024The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024
.jpeg?width=100&auto=webp&quality=80&disable=upscale)
.jpeg?width=400&auto=webp&quality=80&disable=upscale)


