The top 10 vulnerabilities this year were mostly Adobe Flash, followed by Internet Explorer, according to a Recorded Future study.
December 6, 2016
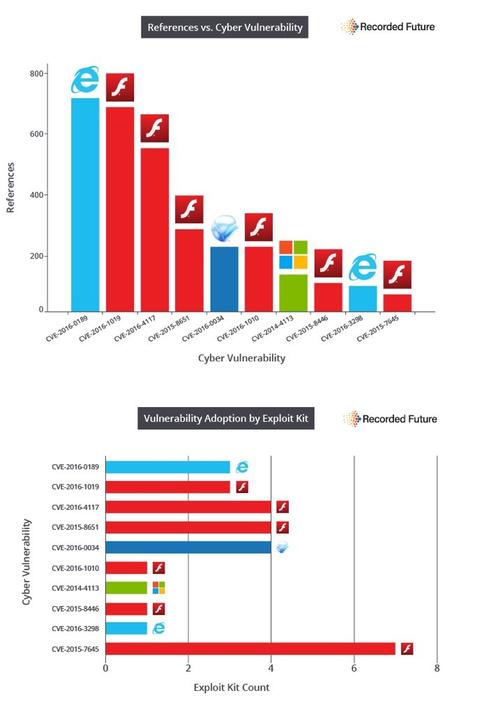
Six of the top 10 vulnerabilities found in cyberattack exploit kits in 2016 were bugs in Adobe Flash Player – including one Flash flaw that was packaged with a whopping seven different exploit kits, new research found.
Recorded Future studied the contents of 141 exploit kits from Nov. 16, 2015 to Nov. 15 of this year, and found that Flash for the second year running led as the application whose vulns were used most in exploit kits; Flash comprised 8 of the top 10 last year.
"A large majority of exploit kits have Adobe Flash Player vulnerabilities, so at the end of the day, not a whole lot has changed" with Flash's prevalence in exploit kits since last year's study, says Scott Donnelly, director of technical solutions at Recorded Future.
Interestingly, the Flash vulnerability found in the most exploit kits by Recorded Future's research, CVE-2015-7645 - which lives in seven exploit kits - was the first zero-day Flash flaw discovered in the wake of Adobe's efforts over the past year to better secure its software with code-structure updates and mitigation features. Adobe worked with Google's Project Zero team to add attack mitigation features to Flash last year.
Meanwhile, Microsoft Internet Explorer, Silverlight, and Windows vulnerabilities also made the top 10 list, with IE's CVE-2016-0189 as the number one flaw found in exploit kits overall. "CVE-2016-0189's impact is tied to multiple version of IE it affects as well as its link to three active exploit kits including Sundown and RIG, which have helped fill the void left by the Angler Exploit Kit," according to Recorded Future's report published today, "New Kit, Same Player: Top 10 Vulnerabilities Used by Exploit Kits in 2016."

Recorded Future also found that the exploit kits that have stepped up to fill the gap of the now-defunct Angler exploit are Sundown, RIG, and Neutrino.
Flash-y
The Flash CVE-2015-7645 flaw affects Windows, Mac, and Linux operating systems, which Recorded Future said makes it especially attractive and "versatile" for attackers. The flaw, which Trend Micro had dubbed a "method confusion" bug, was used by the Russian state hacking group known as Pawn Storm/APT 28/Fancy Bear. The attack group sent spear phishing emails to foreign affairs ministers in various nations and rigged the URLs with exploits that the flaw, which allows an attacker to wrest control of the victim's machine.
Its dominance among exploit kits came as a bit of surprise to researchers since Adobe had been working on better securing its apps. "Theoretically, that was the more secure version" of Adobe software, Donnelly says.
But the vuln is fairly simple to exploit, and isn't always patched, according to Recorded Future. "While the vulnerability was patched by Adobe fairly quickly, its ease of exploitation and the breadth of operating systems affected have kept it active. Unfortunately, slow enterprise patching and lack of knowledge by home users mean the vulnerability still manages to help kits infect machines," the report says.
None of the vulnerabilities that made the top 10 in last year's report were found this year in exploit kits. "These were all new" vulnerabilities, Donnelly says.
Another key finding of the report was that the new exploit kit on the block, Sundown, is making inroads. Sundown, which reuses other kits' exploits, appears to be the handiwork of less sophisticated authors, experts say.
"It's not like Angler and Neutrino, which were written from scratch by sharp guys," says CW Walker, a Recorded Future researcher. "It's gaining a lot of popularity, but it doesn't require the same support as Tier 1, AAA-level exploit kits in the past."
Checklist
Recorded Future says the best bet is to patch the vulns it cites in the report, as well as get rid of any of these affected apps that aren't needed by the business. The security firm in its report also recommends:
Enable "click to play" for Flash
Take a look at running Google Chrome, which benefits from Google Project Zero's work and study of Flash flaws
Deploy browser ad-blockers to protect from malvertisting attacks
Run regular backups, especially for shared files
Related Content:
About the Author(s)
You May Also Like
Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


