To achieve widespread adoption, TPM must overcome challenges to encryption key management.

The Trusted Platform Module is a hardware component built into PCs and laptops. It's designed to securely generate and store encryption keys, passwords, and digital certificates. The Trusted Platform Module, or TPM, can be used for a variety of purposes, such as encrypting files and folders and authenticating users, applications, and computers.
According to IDC, nearly 250 million PCs will have shipped with TPM hardware by 2009. In theory, this level of deployment means the module should be the foundation for a variety of useful applications widely embraced by enterprises and individual users. In reality, there are few apps that take advantage of TPM. A major reason is the complexity of managing TPM itself and encryption keys; another may be a lack of awareness of the module and its capabilities.
The Trusted Platform Module is developed by the Trusted Computing Group, a nonprofit organization that designs and develops open specifications for trusted computing. It has approximately 170 members. The module was designed to help organizations protect sensitive information and enable strong authentication for business use and e-commerce transactions. TPM's hardware-based key-generation capabilities make it very secure against many common attacks.

We'll examine why TPM adoption hasn't matched physical deployments and look at the prospects for wider use of the technology.
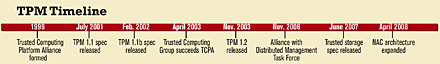
A BRIEF HISTORY OF TPM
Along with some IBM research, Microsoft's Trustworthy Computing initiative drove much of the early work in the development of TPM. Along with a number of other practices, Microsoft envisioned the beginnings of a more secure operating environment that included a hardware-based cryptographic root of trust (see story, "TPM: A Matter Of Trust"). Microsoft called this root the Next-Generation Secure Computing Base. The name that many folks knew it as, however, was the internal code name Palladium, after the mythical statue thought to have protected Troy.
Unfortunately for the Trusted Computing Group, Palladium generated a firestorm of negative feedback. Critics argued that Palladium was primarily designed to take control away from the owner of a computer, and privacy rights advocates were riled up over the fact that it was difficult for TPM to allow sufficiently anonymous verifiable transactions. Fortunately, the 1.2 version of the specification has significantly improved the ability for TPM to be used in a way that maintains privacy while still achieving security.
The primary criticism was that one of the stated design goals of TPM is that it could be used to create supposedly unhackable digital rights management systems. DRM technology aims to prevent users from copying and sharing digital content, such as music and movies. Many in the technology community argue that DRM restricts their fair-use rights and pits users against their own computers.

(click image for larger view)
LOCK IT UP
While a Trusted Platform Module chip could be applied to DRM, it's far from the most common use-case of the technology today. More important in the TPM ecosystem are the other possibilities it affords. The Trusted Computing Group encompasses a variety of platforms, including working groups dedicated to Authentication, Mobile, Software Stack, Storage, Trusted Network Connect, and Virtualized Platform.
The most widespread use of TPM today is Microsoft's BitLocker drive encryption technology. BitLocker can operate with or without the TPM hardware, though the recommended and most secure method of operation requires a 1.2 TPM chip, and it's able to offer significantly more security than non-TPM modes of operation. That's because the keys are secured in the hardware rather than in software, making them harder to tamper with or steal.
Also teaming up with TPM for data encryption are hard drives capable of handling data encryption and decryption internally, such as Seagate Momentus FDE.2 drives. This is one of the few full-disk encryption architectures that would not be vulnerable to the recently publicized "cold-boot" attacks that are able to extract the contents of a computer's memory after it's been powered off and seek out encryption keys.
IDENTITY CHECK
While disk encryption is a popular use for the TPM chip, it may be the user and machine identification features that steal the show in the long run. With support for multifactor authentication features such as an additional PIN or biometric authentication, TPM can serve as the one-stop shop not only for authenticating a user to a machine, but also as an authentication mechanism for Web applications and business applications that would benefit from strong cryptographic authentication.
The Web is one reason the Trusted Computing Group repurposed itself from the original goals of Trusted Computing Platform Alliance back in 2003. Instead of creating a platform for trusted PC computing, it wanted to be able to integrate the same techniques across a wide variety of uses and platforms.
Of course, integrating TPM into the authentication process for a Web application negates one of the values of Web apps in the first place--they're accessible from any Internet-enabled PC.
This problem may be solved by cell phones, which could act as a soft token to authenticate users. For example, if a user wants to access an online banking application from a strange machine, the bank can send a one-time password to the user's phone. The user would enter this password into the banking app. Meanwhile, the entire process is secured against tampering by TPM's hardware-enabled trusted connection from the server to the PC being used.
THE LOWDOWN |
THE PROMISE |
Imagine a software-as-a-service vendor able to leverage a secure hardware token in mobile devices for user authentication. The additional layer would provide a level of security analogous to a secure hardware token with a cost approaching the more inexpensive software token. This assumes, of course, that the SaaS vendor was able to develop a manageable process for enrolling the customer's mobile devices into its encryption infrastructure.
This leads directly into the weak spot for TPM--key management. Managing the keys protected by a TPM chip is almost identical to any other encryption platform. Not only must those TPM-generated keys support the usual enterprise key management features--such as enrollment and revocation, and key recovery in case of lost PINs--but there are issues unique to TPM, such as maintaining system state when upgrading, as changes may upset the ability of the module to produce a valid key for an encrypted system.
Some standalone software tools already are available for IT to manage the Trusted Platform Module. For example, Microsoft offers some free TPM management tools. And a large number of OEMs that manufacture PCs and laptops ship Wave Systems' Embassy Trust Suite, which is capable of providing a variety of services to maintain the module itself. However, more powerful management capabilities might require an upgrade to one of Wave's enterprise-level products.
Even without an enterprise management platform, however, some organizations may be able to take advantage of the number of TPM chips deployed in their environment right now. The Trusted Computing Group Web site offers a series of white papers on using TPM with existing enterprise systems such as wireless networks, VPNs, and network access control.
While it's important to consider the extra management effort involved, it's definitely worth examining what you can use for free with the built-in tools along with the module.
Continue to the sidebar:
TPM: A Matter Of Trust
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024


