Unpatched flaw in iOS enables malicious profile users to secretly control devices and intercept data.
Apple iOS users: Beware malicious profiles that can be hidden by attackers, thus making them extremely difficult to eradicate.
Yair Amit, CTO of Skycure, sounded that warning last week at the RSA conference in San Francisco. Amit delivered a presentation focusing on how an attacker could create a malicious access point name (APN) and cellular data settings file -- stored as a "profile" in the "general" iOS settings menu -- to control devices and intercept data.
These profiles, also known as mobileconfig files, are XML-based files used by telcos, mobile device management (MDM) providers, and some mobile applications to configure everything from WiFi and VPN to email and cellular settings. "When used by mobile device manufacturers and carriers, this is actually a great feature," Amit said in a phone interview.
For example, the APN Changer site allows iPhone and iPad users to load APN -- carrier settings -- profiles that allow them to use unofficial carrier SIMs with their devices. Numerous anecdotal reports have said that AT&T retail store staff members regularly download profiles from the APN Changer website when configuring devices for "pay as you go" iPhone customers.
[Looking to keep spying eyes out of your messages? See Cryptocat Wins Apple Approval.]
Using a VPN connection to a reporter's iPhone, however, Amit demonstrated how -- after an iPhone user loaded a malicious profile -- an attacker could open arbitrary applications, make the browser load arbitrary URLs, or run search queries, and how all traffic flowing to or from the device could be sniffed, no matter whether the individual apps were using SSL/TLS or browsing HTTPS sites. As a result, everything from Facebook to banking sessions could be monitored. Furthermore, if combined with known vulnerabilities in various MDM products, Amit said an attacker could not only subvert an iOS device, but also MDM controls.
"We see a bigger picture, of an attack that can access all of the stuff on your device -- both personal and for business -- and remain undetectable, and for that reason, we find it very important to remind people about these problems, and to be sure they update their operating systems," Amit said.
While the threat of malicious profiles has been known for some time, the vulnerability recently detailed by Skycure would enable an attacker to hide their profile after a user was tricked into installing it. "We recently found a vulnerability on iOS that allows [someone] to make these profiles, once installed, completely hidden, which means that not you or your admin can know that such a profile runs on your device," Amit said.
He declined to demonstrate that vulnerability on the reporter's iPhone -- saying that once the profile was loaded and hidden, it became quite difficult to remove -- and noted that Apple plans to patch the flaw with the release of iOS 7.1. "We will not disclose technical details until iOS 7.1 is released," he said.
Apple Insider reported this week that Apple will likely release iOS 7.1 later this month, which includes a number of features designed to make it easier for IT administrators to automate MDM setup for wireless devices. That feature could be used to configure thousands of devices rapidly, for example in enterprise or educational settings.
But like recent versions of iOS, the update will likely patch not just the hidden-profile vulnerability but also other flaws that might be exploited by attackers, including a background monitoring vulnerability disclosed last month by FireEye, which affects iOS 6 and iOS 7.
Apple released an emergency fix for a "goto fail" SSL/TLS flaw (also known as CVE-2014-1266) on February 25, in the form of iOS 7.0.6. (Apple also fixed the flaw in OS X Mavericks by releasing OS X Mavericks 10.9.2.)
Attackers could exploit the flaw to eavesdrop on the communications of any vulnerable device, provided that the attacker was on the same network or WiFi hotspot as the target.
"To mitigate the risk of this vulnerability it's crucial to notify employees using vulnerable devices that they shouldn't connect to public WiFi access points," said Dirk Sigurdson, director of engineering for Rapid7's Mobilisafe, in a blog post. "It's nearly impossible to discern legitimate public access points from those setup to steal data, and so devices that are vulnerable to this attack should stay on private ones."
The best fix for the flaw is simply to update vulnerable devices to iOS 7.0.6, which runs on the iPhone 4 (and newer devices), iPod Touch (5th generation), and iPad 2 and newer devices. "Don't make the assumption that employees will automatically update their devices to address this issue," Sigurdson said.
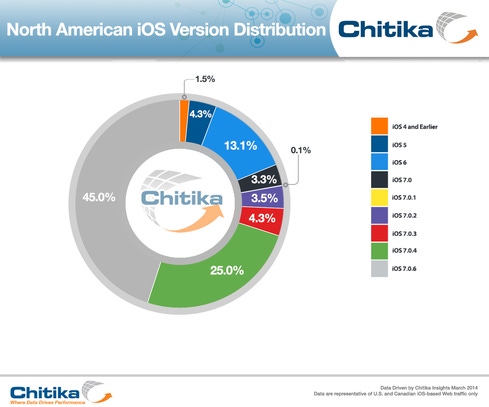
According to a survey of millions of iOS devices in the United States and Canada that are using the web, as of Tuesday, 45% of all iOS users were employing version 7.0.6, Andrew Waber, a market analyst at online advertising network Chitika, said via email. That's a noticeable jump in iOS 7.0.6 from one week ago, when just 20% of users had adopted the latest version of the operating system.
But as of Tuesday, 36% of iPhone and iPad users were still running a version of iOS 7 that was vulnerable to the SSL/TLS goto-fail flaw.
IT is turbocharging BYOD, but mobile security practices lag behind the growing risk. Also in the Mobile Security issue of InformationWeek: These seven factors are shaping the future of identity as we transition to a digital world. (Free registration required.)
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




