Boredom cited as excuse for alleged hack campaign that may have compromised more than 30 government and private sites.

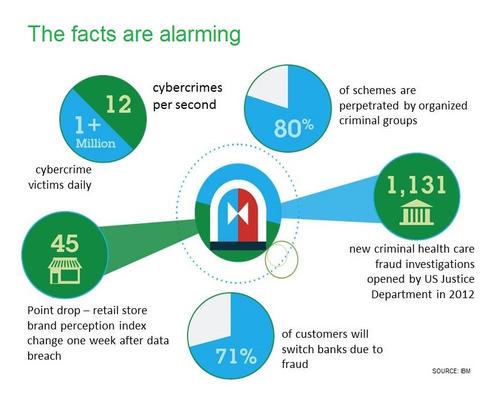
10 Ways To Fight Digital Theft & Fraud
10 Ways To Fight Digital Theft & Fraud (Click image for larger view and slideshow.)
A former US Navy systems administrator is part of a group that's been charged with hacking into 30 different sites and stealing sensitive information, while working in the nuclear reactor department aboard the USS Harry S. Truman aircraft carrier.
A 22-page indictment filed this week in US District Court in Oklahoma charged alleged members of "Team Digi7al" with hacking and stealing sensitive information from sites run by the likes of the Department of Homeland Security, Los Alamos National Laboratory, Harvard University, AT&T U-verse, and the Toronto Police Department.
According to the indictment, the gang comprised at least five people: Nicholas Paul Knight (a.k.a. Inertia, Logic, nickmc01, Solo, INER7IA), 27, a former enlisted Navy member and self-described "nuclear black hat" who handled publicity; Daniel Trenton Krueger (Thor, Orunu, Gambit, Chronius, 7hor, G4mbi7), 20, a network administration student at an Illinois community college who handled the technical side; and three minors -- based in Alabama, Georgia, and Louisiana -- who performed technical hacking work.
If a Team Digi7al Pastebin post is to be believed, however, the group counted eight members: Logic, 7hor, Shr00mi3, Sp3ctrum, Ichi, Kalypto, Th1nkT0k3n, and ThePonyWizard.
[Those serving in the military are twice as likely to fall victim to identity theft as the general public. How can we mitigate the risk? Read Defending Against Identity Theft In The Military.]
Regardless, the group drew the attention of the Naval Criminal Investigative Service (NCIS) after the gang's members began posting to Twitter (@TeamDigi7al) links to dumps of partial personal information pertaining to 20 Navy personnel.
"So heres that #Dump i was talking about. #US #Navy was our target," read a June 17, 2012, post. About a week later, the group also posted a link to the Navy's Smart Web Move site. Launched in June 2001, the web-based service was developed
to help Navy families move their possessions whenever they're relocated, in what the service calls a change of "permanent duty station."
NCIS launched its related investigation in June 2012 and confirmed that the Navy's Smart Web Move website and database, located on servers in Tulsa, Okla., had been breached. The system, which was storing information on approximately 220,000 service members -- including their names, dates of birth, passwords, and Social Security numbers -- was immediately and permanently shut down by the Navy.
Figure 1:  The USS Harry S. Truman
The USS Harry S. Truman
"The Navy quickly identified the breach and tracked down the alleged culprits through their online activity, revealing an extensive computer hacking scheme committed across the country and even abroad," said US attorney Danny C. Williams in a statement released this week.
Knight appears to have still been serving on the nuclear aircraft carrier when he was identified by NCIS. "While aboard the USS Harry S. Truman, Knight conducted unlawful Team Digi7al activities on the Navy's computer and was discharged by the Navy after he was caught trying to hack into a Navy database while at sea," reads the indictment, which also says that Knight had boasted to fellow hackers that he hacked the Navy database "out of boredom."
Team Digi7alhas also been accused of using SQL injection attacks, among other techniques, to steal 4,000 usernames and 200 partial credit cards from Autotrader.com; the "most wanted list" from the City of Montgomery and Alabama Police Department; the entire contents of the email account for the Peruvian ambassador in Bolivia; personal information pertaining to more than 1,000 customers of the website of musician Rashod Holmes; and more than 7,500 usernames and mobile phone numbers of AT&T U-verse customers. According to the indictment, the group also hacked into systems at Los Alamos National Laboratory, but the intrusion was spotted by a system administrator, and they "managed to steal only a small amount of information."
After NCIS executed a search warrant on Knight's house in Virginia in February 2013, according to the indictment, he admitted to some Team Digi7al activities and agreed to cooperate with investigators. But he allegedly then told one of his co-conspirators -- a minor, who wasn't named -- to delete all related data from the co-conspirator's PC hard drive. Likewise, according to the indictment, Krueger attempted to delete related data from his PC hard drive using what's known as a three-pass wipe, which makes the deleted data more difficult to recover.
If convicted of the charges filed against them, Knight and Krueger face up to five years in prison and a $250,000 fine, plus the cost of restitution to victims of the alleged crime. No trial date has been set.
NIST's cyber security framework gives critical-infrastructure operators a new tool to assess readiness. But will operators put this voluntary framework to work? Read the Protecting Critical Infrastructure issue of InformationWeek Government today.
About the Author(s)
You May Also Like
Defending Against Today's Threat Landscape with MDR
April 18, 2024The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




