Just like Fortune 500 companies, attackers are investing in sophisticated measures that let them fly beneath the radar of conventional security.
There's always been a tension between the promise of new technology and peril from its misuse or abuse. Look at the recent iCloud breach. A technology that offers the convenience of accessing photos from any device anywhere in the world, iCloud can also be used by malicious third parties to expose your most intimate moments.
I worry about my kids using technology and how it can be abused to defame, embarrass, or bully in ways not thought possible 20 years ago. Perhaps Steve Jobs was right to limit his children's use of technology. In fact, we probably all know people at work who should have their technology use limited for their own safety. But if the risks of cloud apps and mobile devices cannot be reconciled with a healthy childhood, what makes us think they can exist in a corporation with its legal and regulatory duties? The latest evidence to the contrary is a serious breach at a Fortune 500 customer of Skyhigh Networks, the cloud security company I co-founded.
In this recent attack, criminals used popular consumer cloud video sites to remove a large volume of sensitive data without being detected by conventional security measures like the company's intrusion prevention system. What's new is the sophistication used by the attackers to avoid detection; just as companies have invested heavily in technology to detect and stop breaches, so have attackers become smarter about removing data.
Devilishly clever
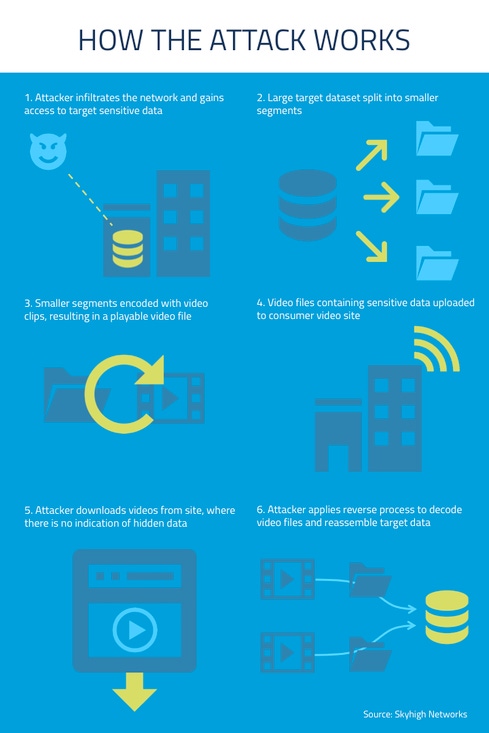
It all started when the company saw an automated alert showing multiple uploads to a video sharing site of identical file sizes. Working with their security team, we discovered attackers were packaging sensitive data into video files and uploading them to a public site where they could be viewed and downloaded. This is a devilishly clever way to steal a lot of data without being detected.
Why? If you want to exfiltrate data from a company, the cloud is a great way to do this undetected since the traffic would appear normal to anyone viewing the company's egress device logs. However, if you want to steal a large volume of data, it's best not to use cloud services like Twitter because even a prolific Twitter user is not likely to send more than 500 tweets per day.
Video sharing sites are the ideal way to steal a lot of data. First off, they're allowed by many companies because they have a legitimate business use. Marketing departments use sites like YouTube and Vimeo to promote the company, while other sites have training videos employees need to be productive. Second, since video files tend to be very large, it's not unusual to see a large file uploaded to one.
In this attack, once hackers gained access to sensitive data stored by the company on the network, they split the data into compressed files of identical sizes, similar to how the RAR archive format transforms a single large archive into several smaller segments. Next, they encrypted this data and wrapped each compressed file with a video file. In doing so, they made the original data unreadable and further obscured it by hiding it inside a video file, a file format where it's not unusual to see multi-gigabyte file sizes. The video files containing stolen data played normally. What was unusual is that each file was an identical size, which is anomalous since encoded videos are usually not the exact same file size.
The attackers then uploaded the videos containing stolen data to a consumer video sharing site. While they're large files, it's not unusual for users to upload video files to these types of sites. However it is unusual to see multiple uploads of identical sizes. If anyone checked, the videos would play normally on the site as well. After the videos were on the site, the attackers presumably downloaded the videos and performed the reverse operation, unpacking each segment of data from the videos and reassembling them to arrive at the original dataset containing the sensitive data they sought to steal. All of this went undetected by the company's array of perimeter defenses and intrusion detection systems.
There's no silver bullet for stopping this type of attack. The standard measures apply: employ a multi-layered security approach that includes network defenses, strong passwords, intrusion detection, and multi-factor authentication to protect sensitive data. The biggest challenge is in detection because identifying these types of data exfiltration events requires manually inspecting uploads to cloud video services -- and even then, this attack was pretty well obfuscated.
Of course, like an over-protective parent, you could block all video services for all but a limited number of employees. But this ignores the fact that people are creative and will eventually find a work around -- as will the attackers.
Bottom line: we are in a guerilla war against an insurgency we are likely never going to totally defeat. This novel data exfiltration technique using video marks an escalation in the conflict as ever more sophisticated attackers adopt the same tools that drive productivity and growth in the corporate world to steal its most sensitive assets.
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




