Chrome users also face subtle attacks, including Chrome extensions that inject unwanted advertisements.

10 Famous Facebook Flops
10 Famous Facebook Flops (Click image for larger view and slideshow.)
Have you ever installed a free software bundle, only to discover that an included application has hijacked your browser settings to reset your default homepage and redirect all of your web traffic through an advertiser-controlled domain name system and search engine?
If so, you're not alone. "Settings hijacking remains our number one user complaint," said Linus Upson, Google's VP of engineering, in a blog post on Friday.
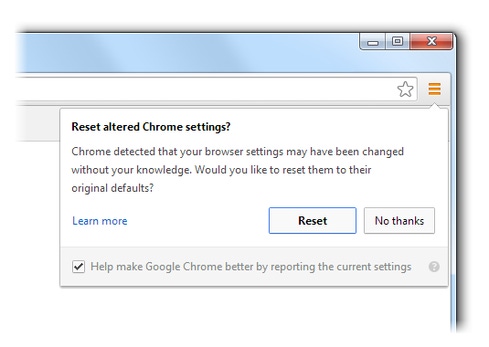
That's despite Chrome -- for both Windows and Mac OS X -- sporting a feature designed to liberate browsers from hijacked settings. "To help keep your browser settings under your control we added a 'reset browser settings' button to Chrome's settings page in October," said Upson. Many Chrome users, however, apparently aren't aware of the feature, which is accessible via the "show advanced settings" link on the browser's settings screen.
Accordingly, "Chrome will be prompting Windows users whose settings appear to have been changed if they'd like to restore their browser settings back to factory default," Upson said. To make that happen, the hijacking alert screen will include the reset button.
Resetting settings is the best starting point for recovering from any browser-hijacking software installation. "I've lost count of the number of times that friends and family have asked me to take a look at their PC 'because it's acting funny', only to discover that their browser has been meddled with by something like Babylon Toolbar, CoolWebSearch or Conduit Search," said security expert Graham Cluley in a blog post.
"Browser-hijacking software like these are often bundled with third-party applications, and can be installed at the same time if the user isn't careful, changing your browser's homepage, displaying irritating hard-to-remove pop-up adverts, or redirecting search queries and displaying sponsored links -- all with the intention of earning more revenue for the people behind them," said Cluley.
Resetting settings is a bit of a nuclear option: All search engines -- including saved ones -- will be reset, the homepage will disappear, all default startup tabs will be wiped, and cookies and site data deleted. All installed apps, extensions, and themes will also be disabled, although they can be set to start again at launch, by default, via the settings menu.
[It's boom times for security startups. Check out 20 Security Startups To Watch.]
After a browser hijacking, however, even a settings reset might not be enough to nuke the underlying scamware. "Resetting your browser's settings does not necessarily mean that you have succeeded in removing the adware which messed with your settings in the first place -- these typically survive rebooting, and the hijack could occur again," Cluley said.
For anyone facing serial hijacking episodes -- even after attempting to reset their settings -- Google's Upson recommends that they visit the Chrome help forum for advice about how to completely excise the offending software.
While the campaign to roll back browser hijackings continues, Chrome users have also been facing an ongoing security threat in the form of scam browser extensions. Jason Ding, a research scientist at Barracuda Labs, warned in a blog post Monday that a group of malicious extension developers -- formerly registered with Google under the developer name of "www.playook.info," but now using the name "www.konplayer.com" -- in recent weeks sneaked 12 Chrome extensions onto the Chrome Web Store.
The extensions, which have been collectively installed by more than 180,000 Chrome users, inject advertisements for 44 different websites -- including chrome.plantsvszombies.com, bejeweled.popcap.com, and myhappygames -- into affected browsers. The group behind the extensions likely earns a referral commission for every user that visits one of the websites that it's advertising.
How did the Chrome security team miss the fact that these extensions are being used to spam whoever installs them with unwanted advertisements, and does Google plan to nuke the 12 extensions? A Google spokesman didn't immediately respond to an emailed request for comment. But Barracuda's Ding noted that the Konplayer group, rather than including the advertising-network-summoning JavaScript in their extensions, employed a measure of stealth by setting their extensions to download obfuscated JavaScript from www.chromeadserver.com. While that site includes the word "chrome" in its URL, it's likely controlled by the Konplayer group.
Security experts have long sounded security warnings about Chrome extensions.
Felix "FX" Lindner, head of Recurity Labs in Berlin, for example, has warned that because Chrome extensions can inject JavaScript directly into Chrome, which is written in JavaScript, they offer would-be attackers enormous malicious potential.
Accordingly, users should beware granting permissions to any Chrome extension. For example, Ding said that each of the 12 recently discovered spamming Chrome extensions requires users to grant them the "your data on all websites" permission before they can be installed "so that the ads can be injected to any websites the users browse."
"Chrome users have to learn to protect themselves," Ding said. "...be very careful if you intend to install Chrome extensions -- even if it is from the Google Chrome web store. Use some common sense to judge whether you need to grant permissions to any extensions. If any of the permissions seem beyond the fence of what it should do, do not install it."
Having a wealth of data is a good thing -- if you can make sense of it. Most companies are challenged with aggregating and analyzing the plethora of data being generated by their security applications and devices. This Dark Reading report, How Existing Security Data Can Help ID Potential Attacks, recommends how to effectively leverage security data in order to make informed decisions and spot areas of vulnerability. (Free registration required.)
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




