NSA denies prior knowledge of the Heartbleed vulnerability, but the White House reserves the right to withhold zero-day exploit information in some cases involving security or law enforcement.

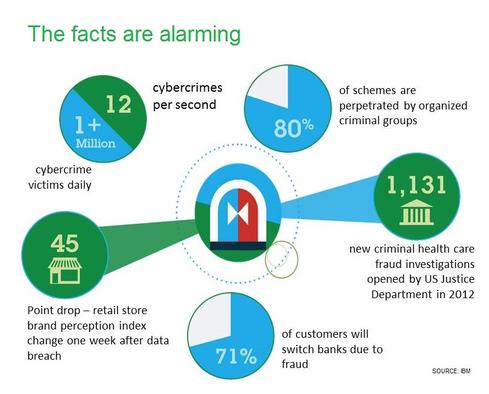
10 Ways To Fight Digital Theft & Fraud
10 Ways To Fight Digital Theft & Fraud (Click image for larger view and slideshow.)
The White House and National Security Agency have strongly denied reports that the NSA had known about the Heartbleed vulnerability in OpenSSL for years and was actively exploiting it for intelligence-gathering purposes.
Those allegations appeared Friday in a Bloomberg News report -- citing unnamed sources -- claiming the NSA kept secret details about the Heartbleed vulnerability for at least two years. The vulnerability (a.k.a. CVE-2014-0160), which can be used to spoof and steal encrypted information from millions of vulnerable websites, was recently discovered and made public by Google engineer Neel Mehta and Finnish security firm Codenomicon.
But the NSA -- via Twitter -- and the Obama administration quickly disputed the Bloomberg report. "NSA was not aware of the recently identified vulnerability in OpenSSL, the so-called Heartbleed vulnerability, until it was made public in a private sector cybersecurity report," read a statement released Friday by the Office of the Director of National Intelligence (ODNI). "Reports that say otherwise are wrong." The ODNI also noted that the federal government relies on OpenSSL to secure government websites, and claimed that if any agency -- including the NSA -- had previously discovered the vulnerability, "it would have been disclosed to the community responsible for OpenSSL."
[How does Heartbleed affect your enterprise's internal network? Read Heartbleed's Intranet & VPN Connection.]
The discovery of the Heartbleed bug has triggered questions about how fast government agencies should come clean if and when they discover a never-before-seen bug. On that front, Richard Clarke, a member of a presidential panel that reviewed the NSA's practices and issued specific recommendations to the White House, told Bloomberg News that three weeks ago, President Obama told government agencies that -- in most cases -- if they discover a zero-day vulnerability, the information will be publicly disclosed.
The ODNI statement issued Friday echoed that instruction, saying that going forward, agencies would be "biased toward responsibly disclosing such vulnerabilities" using a predefined inter-agency review known as the Vulnerabilities Equities Process.
But the Obama administration also reserved the right to withhold zero-day vulnerability information for cases where "there is a clear national security or law enforcement need."
Some privacy experts questioned the leeway that the White House left intelligence agencies such as the NSA. "The policy has a loophole so big that you could drive a truck through it," Christopher Soghoian, principal technologist at the American Civil Liberties Union, told Bloomberg News. On the other hand, he said, the fact that the president is even discussing zero-day policies represents "a really big shift."
But some security experts have argued that, by definition, it's not the job of the NSA -- or any other country's intelligence service -- to publicly share information about zero-day threats. Errata Security CEO Robert David Graham pointed out that the existence of the Heartbleed bug was hardly the NSA's fault, and if the agency did decline to warn OpenSSL or anyone else about the flaw, that was well within its remit. "Finding such bugs and keeping them quiet is wholly within the NSA's mission statement," he said in a blog post. "Their job is to spy on foreigners and keep state secrets safe. Generally, state secrets aren't on machines exposed to the Internet, so keeping the bug secret had no impact on that."
Furthermore, the NSA may not have needed Heartbleed. Documents leaked by Edward Snowden, for example, revealed the existence of a top-secret NSA program code-named BULLRUN, which was designed to defeat specific encryption protocols, including SSL. A recent Bloomberg News report, furthermore, cited two unnamed sources who claimed that the NSA has at least two techniques for defeating SSL.
The discovery of the OpenSSL vulnerability has led millions of consumers to change their online passwords and prompted businesses to put costly fixes in place. The flaw exists in versions 1.0.1 and 1.0.2 beta of OpenSSL, which is an open-source implementation of the SSL and TLS protocols that provide websites with cryptographic capabilities. In recent days, both researchers and attackers have demonstrated how the vulnerability can be easily -- if not immediately -- exploited to recover a site's private keys.
As of last week, Netcraft reported that about 500 million websites are vulnerable to the Heartbleed bug. By Monday, only about 30,000 vulnerable sites had reportedly changed their digital certificates; the rest remain vulnerable to Heartbleed.
Cyber-criminals wielding APTs have plenty of innovative techniques to evade network and endpoint defenses. It's scary stuff, and ignorance is definitely not bliss. How to fight back? Think security that's distributed, stratified, and adaptive. Read our Advanced Attacks Demand New Defenses report today (free registration required).
About the Author(s)
You May Also Like
The fuel in the new AI race: Data
April 23, 2024Securing Code in the Age of AI
April 24, 2024Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




