Most organizations already have the tools for starting a low-cost, high-return Dark Web cyber intelligence program within their existing IT and cybersecurity teams. Here’s how.
Blind spots are everywhere in cybersecurity. To make it worse, the threats are increasing in both form and frequency and it’s a daily struggle to defend against threats you can’t see coming. From traditional malware infections and active network attacks to new kinds of social engineering spear-phishing and novel hardware exploits, attack vectors evolve right along with your company’s risk surfaces. You evolve, they evolve – it’s a continuous cycle.
Finding information on these threats is a dynamic, moving target and there isn’t any one-stop source or service that gives you all you need to know. Worse, the details are full of irrelevant, noisy information, nearly impossible to decipher.
For most companies, shedding light on these areas of cyber defense is increasingly being accomplished by standing up expensive cyber intelligence initiatives such as threat intelligence (at varying low-to-high levels), risk intelligence and traditional human (HUMINT) activities. Companies are buying data, acquiring tools, and hiring pricey investigators and cyber analysts to build up their own miniature intelligence agencies. This is an expensive operation. Plus, both the field and approach is so immature in the private sector, it’s hard to know which activities will provide any real return on what is becoming a very significant investment even for individual parts of an "intelligence program."
Surprisingly, for what is perhaps the "darkest" of the blind spots, the Dark Web, can be one of the easiest to overcome.
The Dark Web is veritably tiny in comparison to the more familiar public Web and miniscule when compared to the larger Deep Web that is not searchable by search engines. When most people think of the Dark Web, they immediately think of trade in drugs and pornography. While those are indeed the predominate commodities in a space built for illicit commerce and trade, the Dark Web offers other things too, including:
Hacking for Hire (along with resumes of prior conquests and targets)
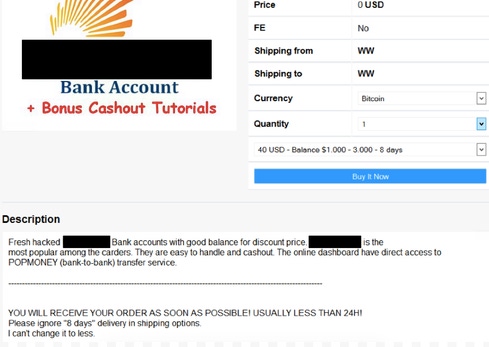
General and Specific Cyber Exploits for Sale (malware aimed at particular tech targets, businesses or industries)
Vulnerabilities for Sale (hacked accounts, back-doors and many more)
Stolen Intellectual Property, Designs and Counterfeits (everything from stolen electronics designs to shoes to fake pharmaceuticals)
Spam and Phishing Campaigns for Hire (Twitter targeting, malvertising and more)
Doxxing and Investigation for Hire (Is your competition snooping on you?)
Hacktivist (and other) Targeting Forums (Who’s about to get hit with a DDOS? The Dark Web is very good for gossip.)
Insider Threat for Hire (Who’s got a grudge for sale against whom?)
In other words, the Dark Web can be thought of as a small pond rich with prized game fish for an organization trying to bolster its defenses. Start monitoring activities on Dark Web sites. Find out what may have been stolen or used against you and improve your overall security posture to close the infiltration hole.
When you go looking, the data found in the Dark Web is almost always highly relevant to you and your business. Because you (presumably) know you, your employees, your products, your customers, your IT, your supply chain, you have all the information you need to begin filtering through Dark Web data looking for things that really matter.
And the things you find do matter, quite a lot.
Thousands of Dark Web index sites exist on the open web and, once you’re in, you’ll find thousands more. Because most of the sites are set up to do illicit e-commerce the black market way, they’re pretty easy to find and use. After searching, you’ll soon find information that can have significant impacts on your business concerns such as your finances, of course, but other areas, too – like your brand and reputation, customer loyalty, life’s blood intellectual property, product development, legal defenses, sales, software and hardware baselines, cybersecurity strategy and acquisition, and a litany of other very important - not just cyber – concerns.
If there is a silver lining in all of this, it’s that most businesses already have all the tools on hand for starting a low-cost, high-return Dark Web intelligence operations within their own existing IT and cybersecurity teams. I have personally been a part of Dark Web data mining operations set-up, implementation and being productive in just a day’s time.
Setting up your own Dark Web mining environment using TOR, private browsing on air gapped terminals via sequestered virtual machine clusters (VMs), is something that’s well-understood among cybersecurity professionals already on your team. When you pair them with the security analysts and intelligence personnel you’re hiring to staff up your cyber intelligence initiatives, it becomes something you can start almost in complete logistic (and fiscal) parallel with these other efforts.
Further, once you’re up and running, collecting and storing this information in a standard way -- the same way you do other cyber event, incident and alert data -- means it’s possible to begin creating a long-term data repository that can be mined and analyzed to perform forensics, predictive analysis, root-cause analysis, and other analytic activities that help you get better organized in your other, more traditional cyber defense operations. Those who don’t are losing out.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




