Human traffickers, crowd-sourcing murderers, child pornographers, and governments in the market for juicy zero-days are flooding the Dark Web -- making it hard for the good guys to defend it.
It can take 30 seconds to load just one webpage on the Darknet. There are only between 200,000 and 400,000 sites in it, but good luck finding the one you want when the only things that remotely resemble search engines are full of phony or out-of-date links. Who would use something so frustrating?
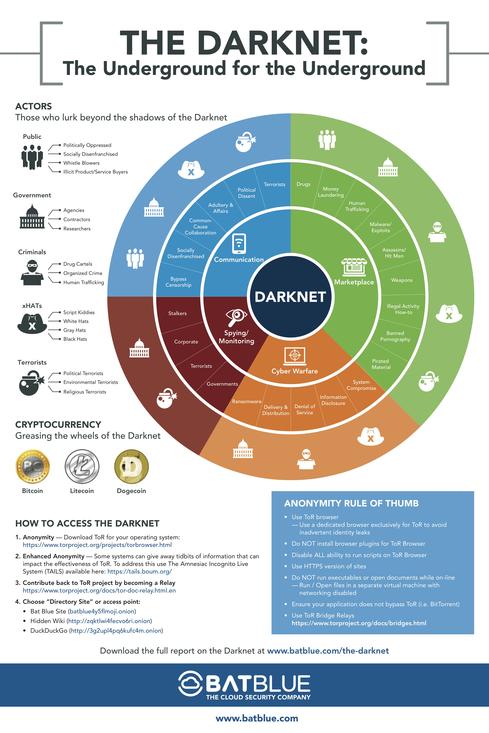
Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of the Internet where the sites are unindexed and accessible only through the onion router (TOR) network.
First and foremost, they found a wide assortment of criminal marketplaces -- for human trafficking, child pornography, and murder.
Babak Pasdar, ethical hacker and CEO of Bat Blue, says that one of the most surprising findings in the research is "how innovative folks have gotten in gamifying certain acts, such as murder." He describes how some sites offer prizes for proof of kills.
From the report: "The Darknet is also a platform for new and innovative ways to commit crime. Empowered by the Darknet’s global reach and emboldened by the anonymity it offers, gamification and crowdfunding of crimes like murder and human trafficking represent an increasingly grim aspect of the Darknet."
As Gillian Ibach, Bat Blue lead cyber intelligence analyst explains, there is no honor among thieves. The lawlessness of the Darknet is so pervasive, that the criminals are scamming each other. She points to the example of human trafficking site Black Death requiring buyers to submit Bitcoin deposits in order to bid on "Nicole" -- an 18-year-old American girl whom the Bat Blue researchers believe didn't actually exist. The report cites other examples of sites that shut down suddenly, and made off with all the Bitcoins left in their customers' escrow accounts.
In addition to the traditional crimes, of course, there were marketplaces for cybercrime -- and government agencies were among the buyers.
"What's most surprising is how engaged and involved governments are in supporting and growing the Darknet," says Pasdar. As he explains, although the FBI and other government agencies are often shutting these sites down, they're also keen to be a part of the marketplace where some of the juiciest zero-day exploits will be bought and sold. "They want to be first to have dibs on it."
Of course, the Darknet is not just a place where illicit goods are bought and sold.
"It's also a platform for people who are desperate," says Pasdar, explaining the necessity of the Darknet's anonymity for individuals who live in oppressive governments. "They need a means and a method to communicate."
As the report states: "The United States government has a complex relationship with the Darknet. ... the U.S. Naval Research Laboratory originally created and released TOR browser. The U.S. government continues to research ways to anonymously browse the Internet and release new technology. The United States also releases new technology to foreign populations to promote dissidence against authoritarian regimes. At the same time, intelligence agencies monitor activity and attempt to trace TOR users for their own strategic purposes."
Although the U.S. may actively release TOR technology to foreign populations, there was some mild unrest recently when an American library decided to host a TOR relay node, to allow its visitors to surf the web anonymously, and access the Darknet. After Ars Technica ran a story about the Kilton Public Library in Lebanon, N.H. becoming the first library on the TOR network, the U.S. Department of Homeland Security reached out to the library's local police department to notify them about the dangers related to child exploitation on the dark web. (According to a report released in June by Trend Micro's Forward-Looking Threat Research Team, a startling 26 percent of the sites on the Darknet are child exploitation sites.)
The library volunteered to take down the TOR node until the library trustees could vote on it. Tuesday, the library trustees voted to restore TOR service, citing its usefulness not only to people in oppressive government regimes, but also to those suffering from domestic abuse. As the Concord Monitor reported:
"With any freedom there is risk,' library board Chairman Francis Oscadal said. 'It came to me that I could vote in favor of the good . . . or I could vote against the bad.
“I’d rather vote for the good because there is value to this.”
Pasdar is suspicious of the DHS's motivations for alerting the local police about the library's TOR node. "My concern is that government has other motives for doing what they're doing," he says. As he explains, government agencies might publicly discourage others to use onion routing -- because it inhibits intelligence agencies' ability to conduct surveillance -- and yet they may be happy to use the Darknet themselves, to shop on the marketplace for cyberweaponry. "I don't think they're as kind-hearted as they seem."
See the full report at batblue.com/the-darknet.
About the Author(s)
You May Also Like
Beyond Spam Filters and Firewalls: Preventing Business Email Compromises in the Modern Enterprise
April 30, 2024Key Findings from the State of AppSec Report 2024
May 7, 2024Is AI Identifying Threats to Your Network?
May 14, 2024Where and Why Threat Intelligence Makes Sense for Your Enterprise Security Strategy
May 15, 2024Safeguarding Political Campaigns: Defending Against Mass Phishing Attacks
May 16, 2024
Black Hat USA - August 3-8 - Learn More
August 3, 2024Cybersecurity's Hottest New Technologies: What You Need To Know
March 21, 2024




